cryptography - What algorithms are used in Bluetooth Secure Simple Pairing LE for authentication, key generation and encryption? - Information Security Stack Exchange

cryptography - What algorithms are used in Bluetooth Secure Simple Pairing LE for authentication, key generation and encryption? - Information Security Stack Exchange
![PDF] A New Design of Algorithm for Enhancing Security in Bluetooth Communication with Triple DES | Semantic Scholar PDF] A New Design of Algorithm for Enhancing Security in Bluetooth Communication with Triple DES | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3db2540a76d0860fc8b8d0fb570f045469c59884/4-Figure6-1.png)
PDF] A New Design of Algorithm for Enhancing Security in Bluetooth Communication with Triple DES | Semantic Scholar

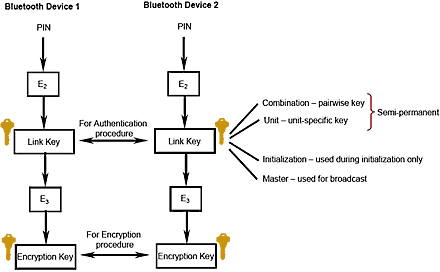
How are initialization keys, combination keys and encryption keys generated in Bluetooth? - The Security Buddy
![PDF] Novel Hybrid Encryption Algorithm Based on Aes, RSA, and Twofish for Bluetooth Encryption | Semantic Scholar PDF] Novel Hybrid Encryption Algorithm Based on Aes, RSA, and Twofish for Bluetooth Encryption | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/86640791499547b12e82d2cfeace1b5d7bebc8d6/6-Figure1-1.png)
PDF] Novel Hybrid Encryption Algorithm Based on Aes, RSA, and Twofish for Bluetooth Encryption | Semantic Scholar
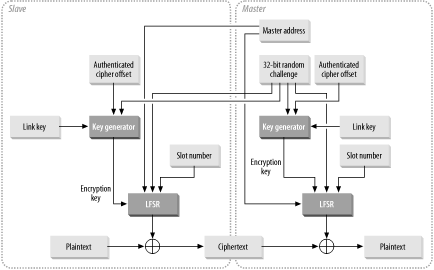
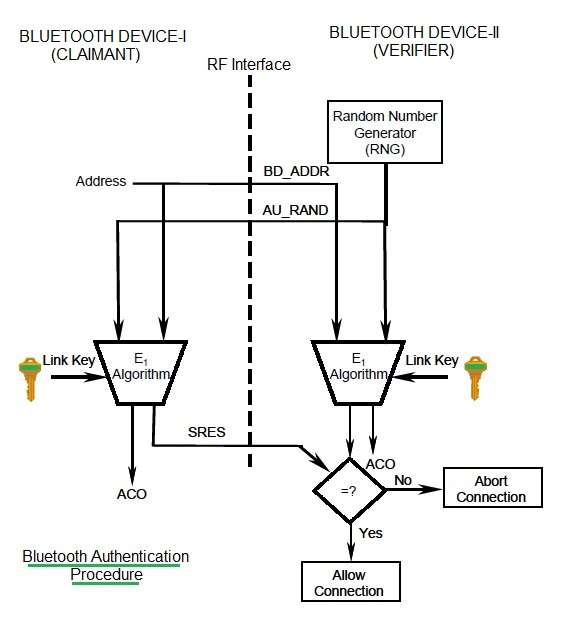
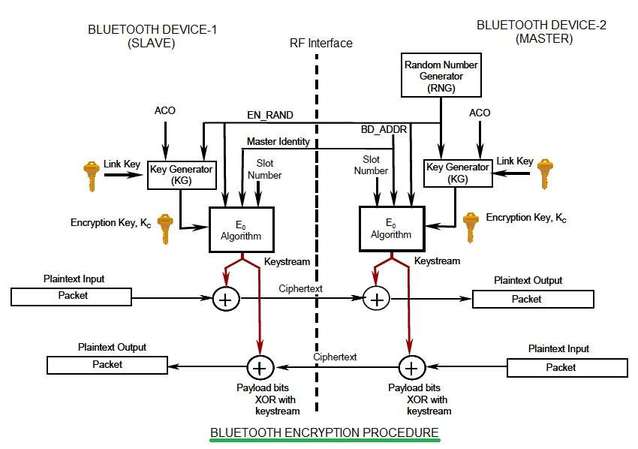
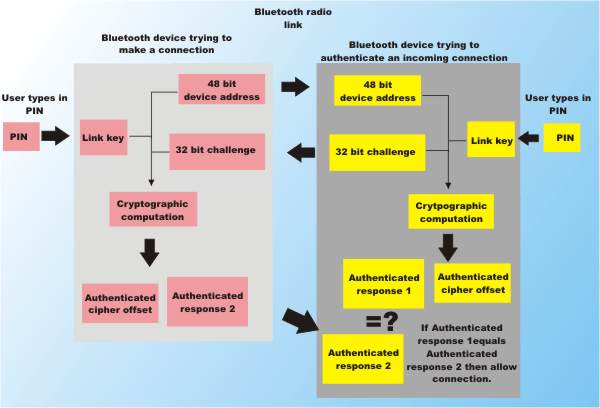
6.7 Bluetooth Security :: Chapter 6. Bluetooth :: Windows XP unwired :: Microsoft Products :: eTutorials.org

PDF) An Integrated Encryption Scheme Used in Bluetooth Communication Mechanism | Bhoopendra Rajput - Academia.edu

Figure 2 from Bluetooth Communication using Hybrid Encryption Algorithm based on AES and RSA | Semantic Scholar