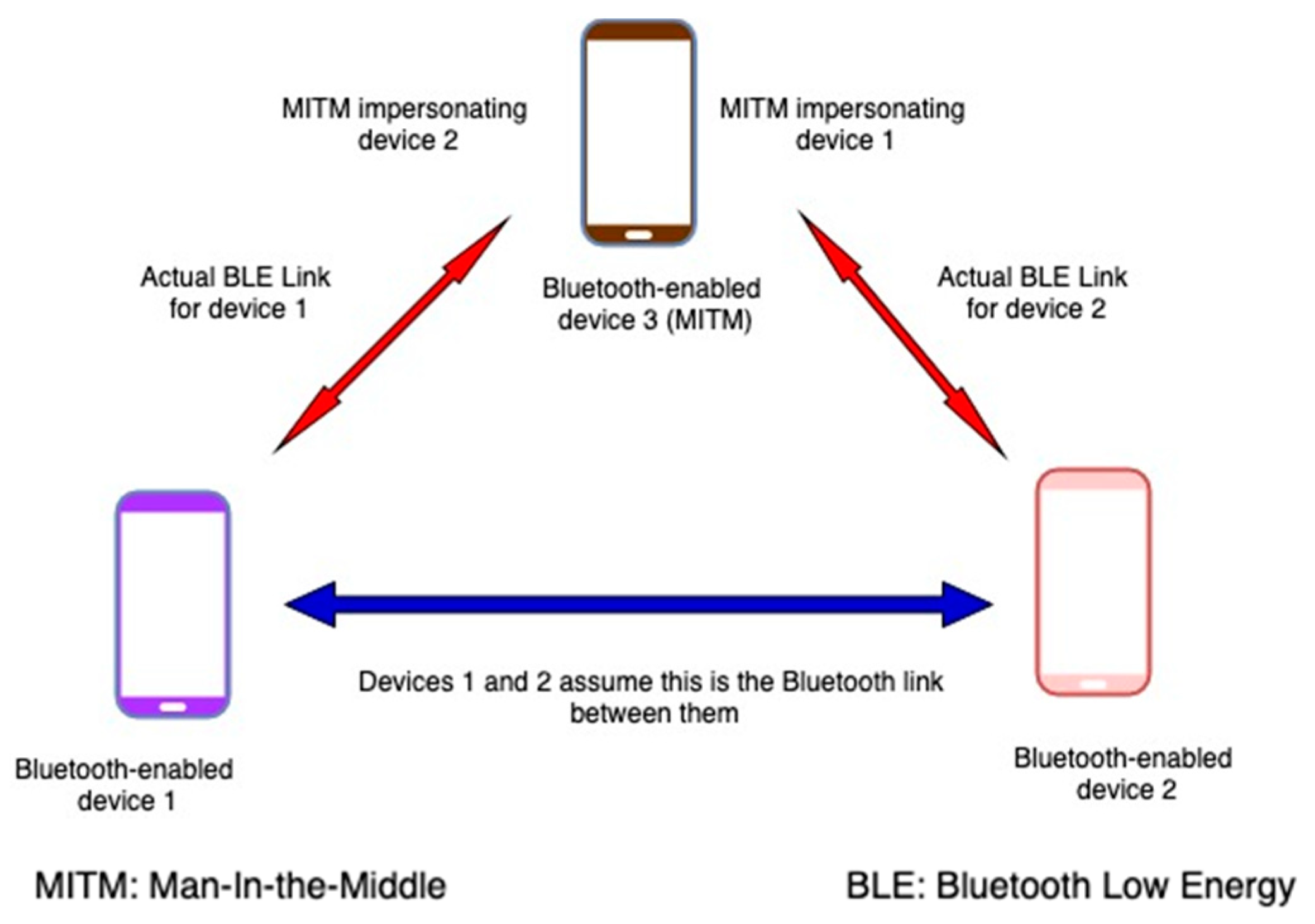
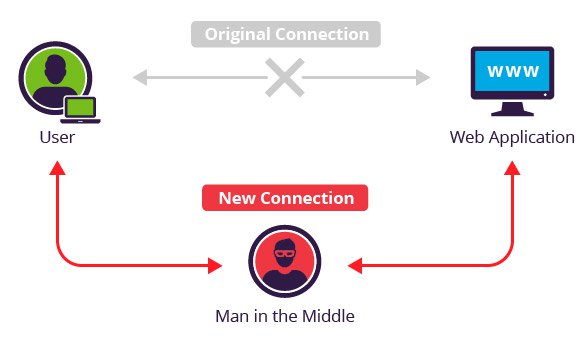
Figure 1 from Effects of Man in the Middle (MITM) Attack on Bit Error Rate of Bluetooth System | Semantic Scholar
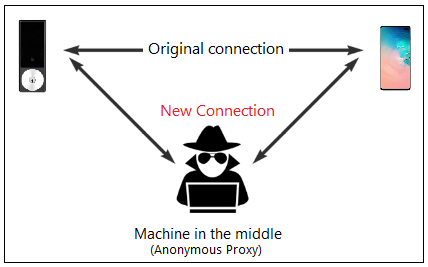
![PDF] A Novel Bluetooth Man-In-The-Middle Attack Based On SSP using OOB Association model | Semantic Scholar PDF] A Novel Bluetooth Man-In-The-Middle Attack Based On SSP using OOB Association model | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/58bf1873844a200e705c37e28a746ae3343a8eeb/3-Figure2-1.png)
PDF] A Novel Bluetooth Man-In-The-Middle Attack Based On SSP using OOB Association model | Semantic Scholar

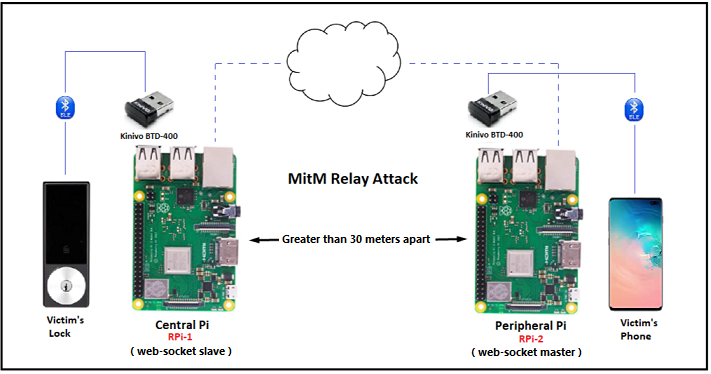
Figure 2 from Man-In-The-Middle attacks on bluetooth: a comparative analysis, a novel attack, and countermeasures | Semantic Scholar