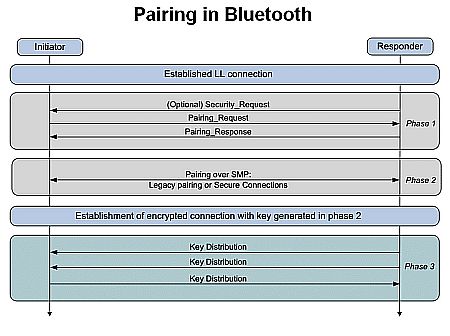
cryptography - What algorithms are used in Bluetooth Secure Simple Pairing LE for authentication, key generation and encryption? - Information Security Stack Exchange

Block Diagram of Bluetooth Encryption The Bluetooth has three different... | Download Scientific Diagram

encryption - How secure is the wireless Bluetooth data stream going from my computer to my headphones? - Information Security Stack Exchange
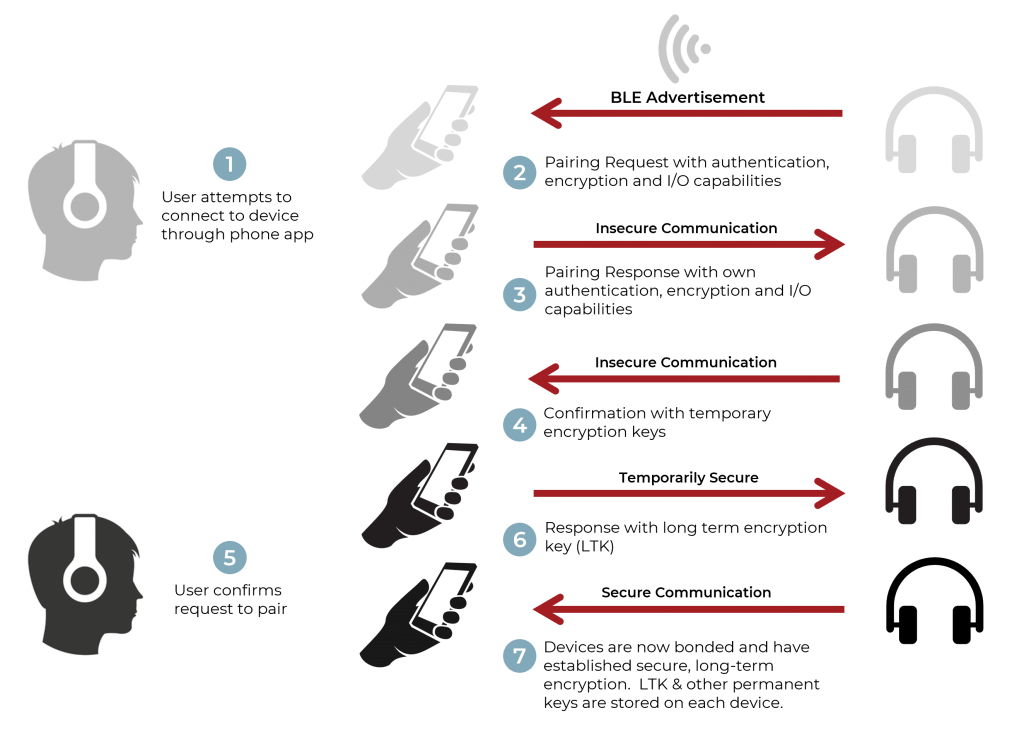
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak

SecureDrive BT (Bluetooth) Hard Drive Hardware Encrypted External Portable Hard Drive - Professional Dictation | Commercial Shredders, Paper Handling | Inventory Trackers | Scales | by Wheeler Business Machines




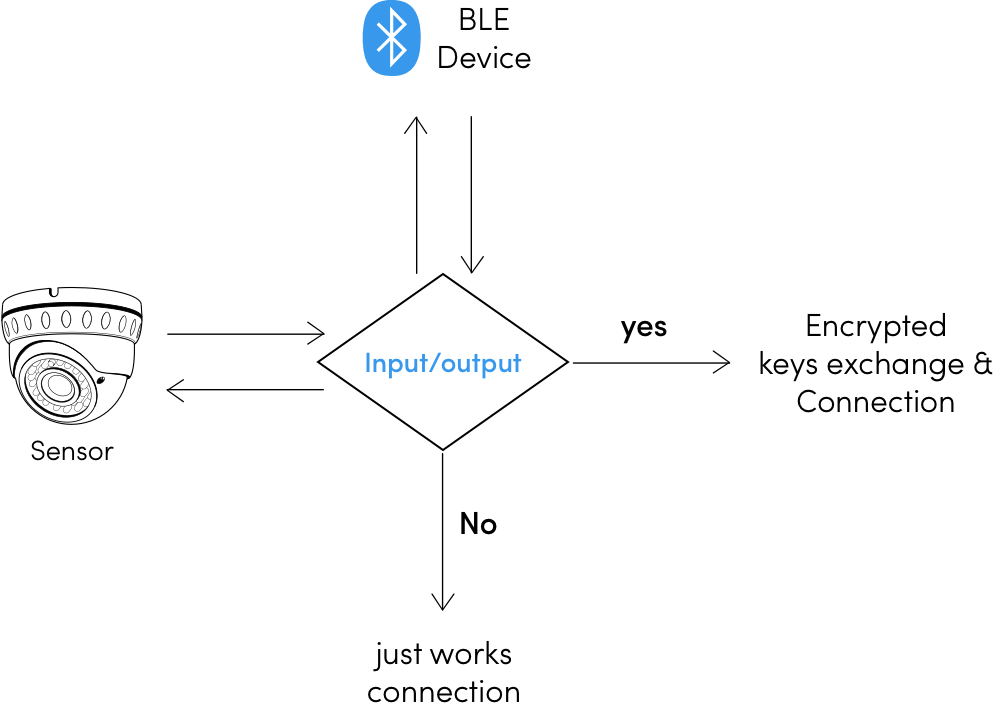
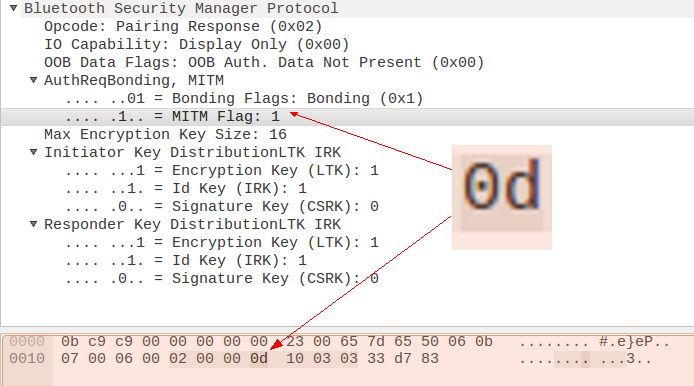

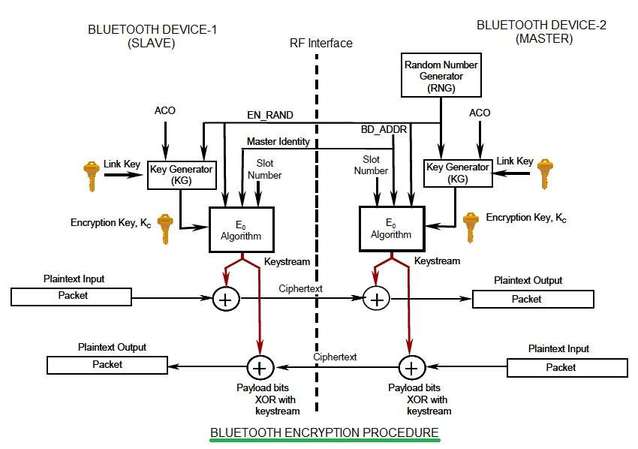

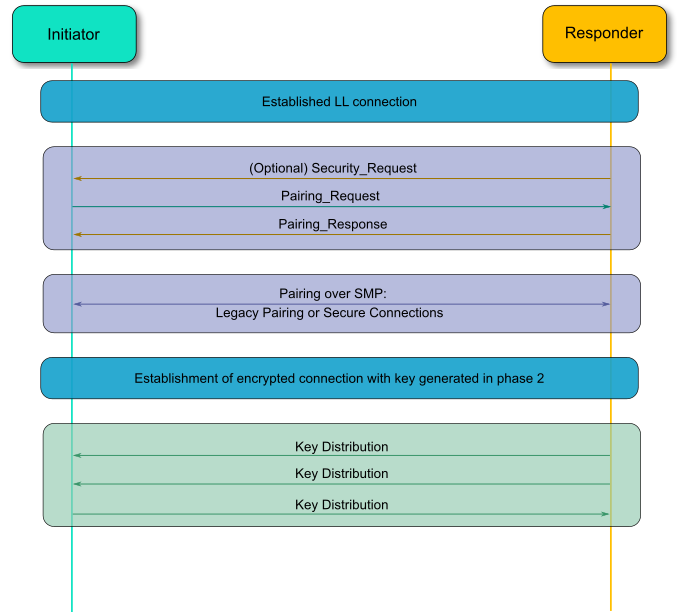


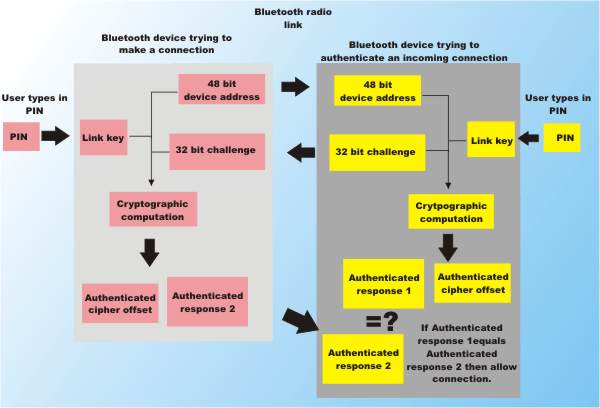
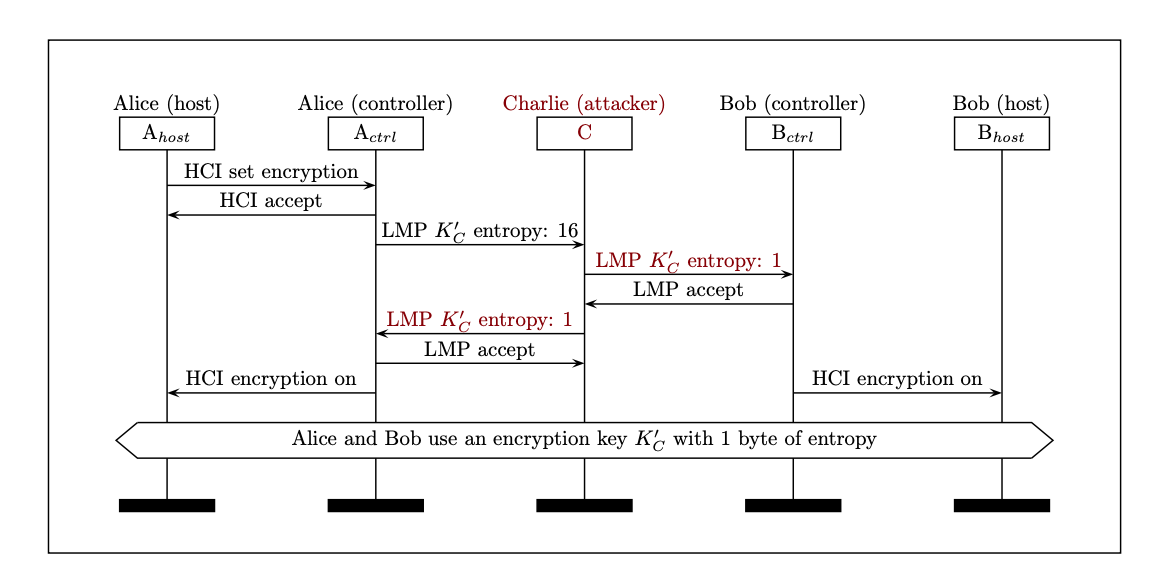


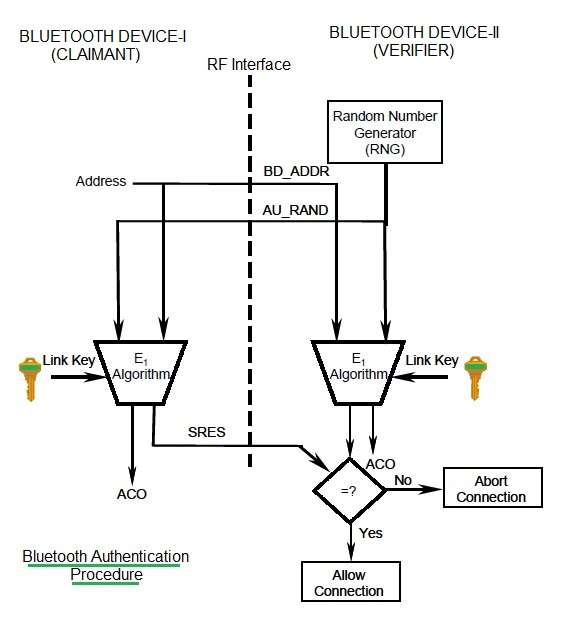
![PDF] Guide to Bluetooth Security | Semantic Scholar PDF] Guide to Bluetooth Security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8e0d28bc4e06050d6d18fb294b505a828749a5ff/37-Figure3-8-1.png)