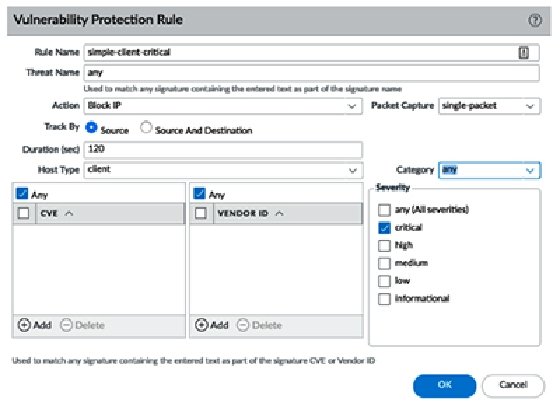
How to Use a Vulnerability Protection Profile to Block a .exe F... - Knowledge Base - Palo Alto Networks

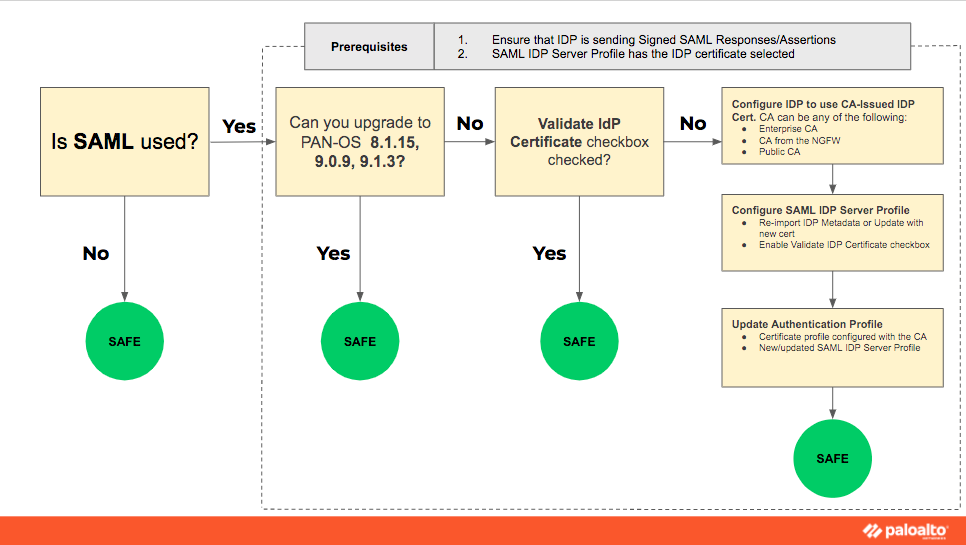
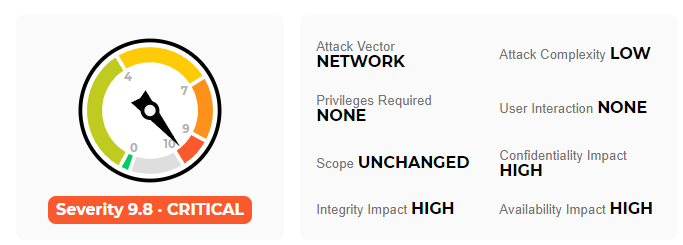
CVE-2020-2021: Palo Alto Networks PAN-OS Vulnerable to Critical Authentication Bypass Vulnerability - Blog | Tenable®

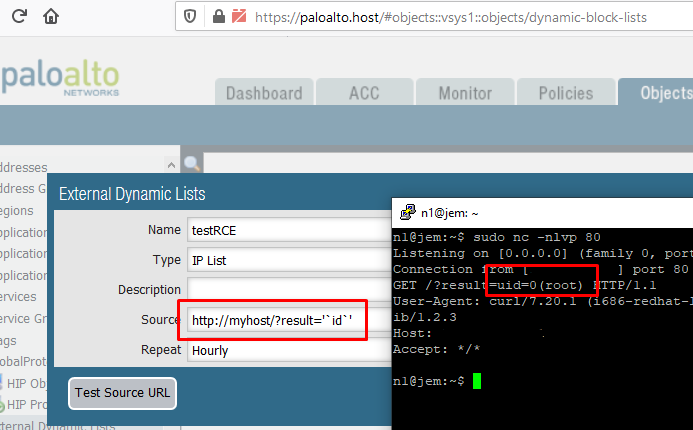
PAN-OS Critical Buffer Overflow Vulnerability (CVE-2020-2040) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR® | Qualys Security Blog

PAN-OS Critical Buffer Overflow Vulnerability (CVE-2020-2040) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR® | Qualys Security Blog