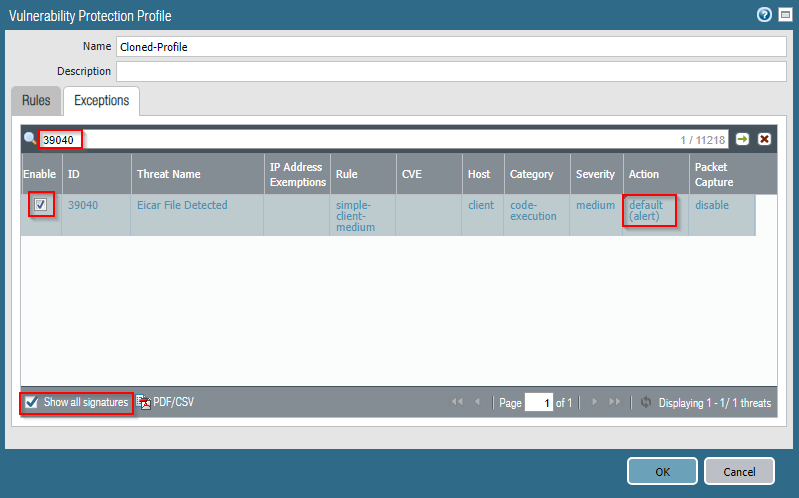
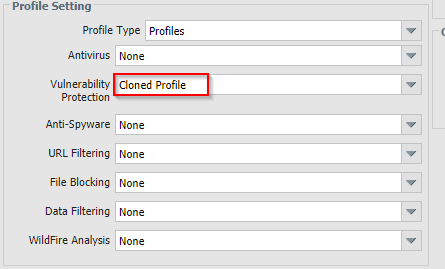
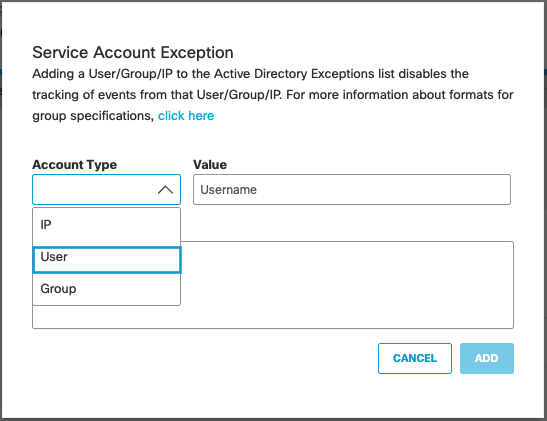
How to Use Anti-Spyware, Vulnerability and Antivirus Exceptions... - Knowledge Base - Palo Alto Networks
Vulnerability Exception Based Upon Source and Destination IP Ad... - Knowledge Base - Palo Alto Networks

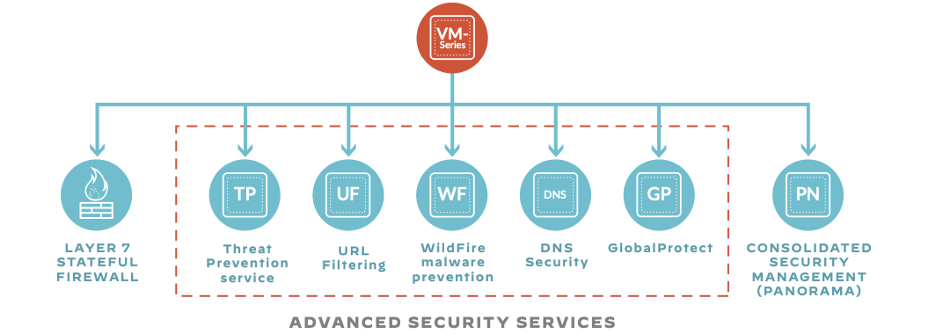
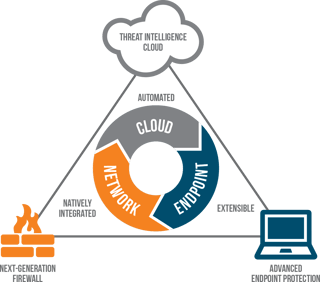
Palo Alto Networks Enterprise Subscription Bundle (Threat Prevention, Advanced URL Filtering, Wildfire, DNS Security, SD-WAN, IOT Security and SaaS Security Inline) | DGF Technologie