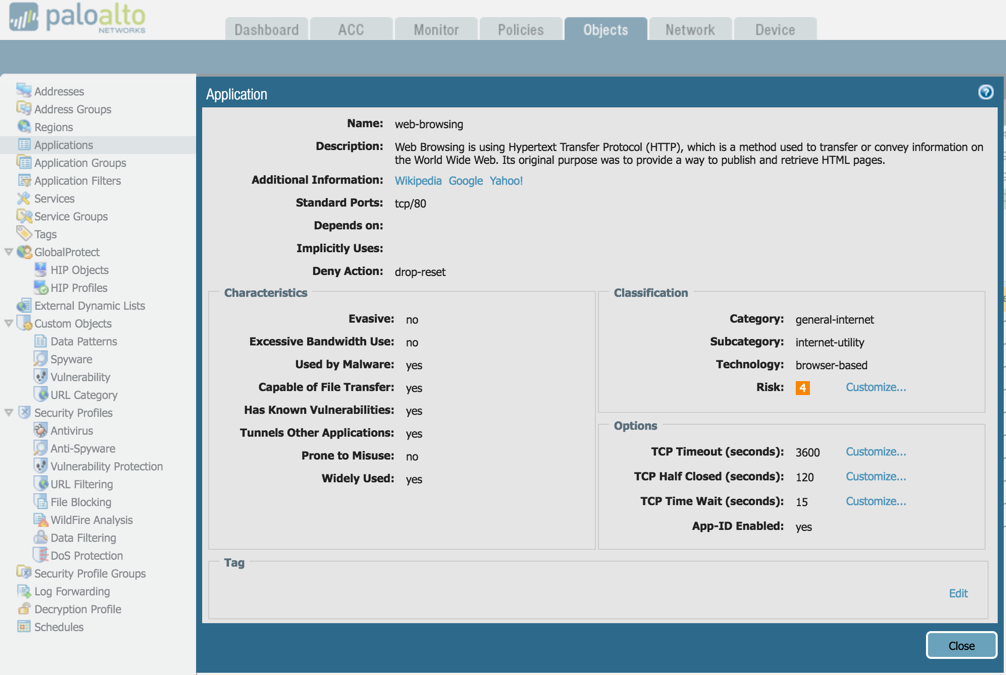
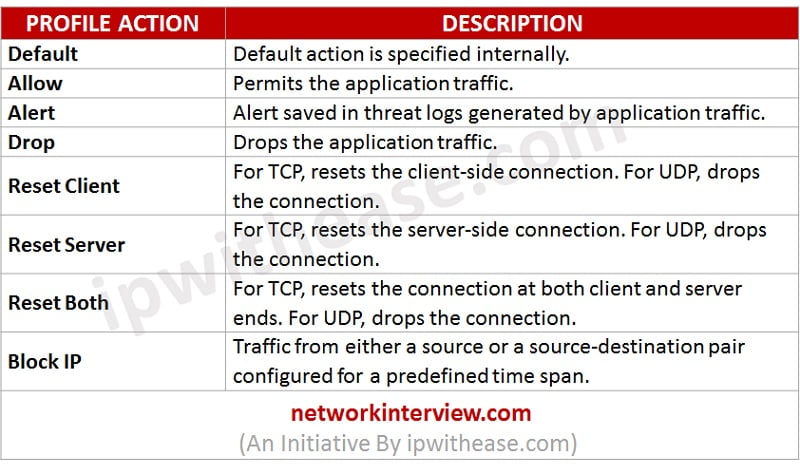
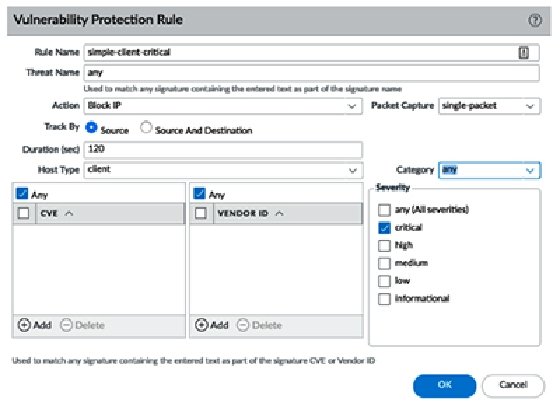
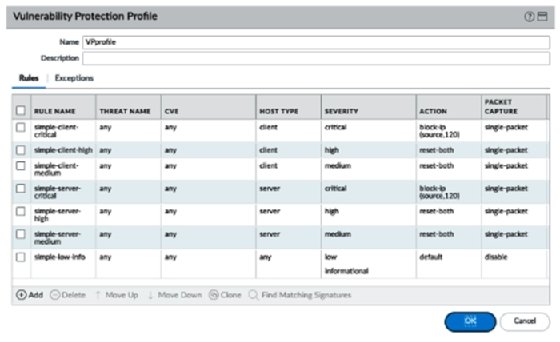
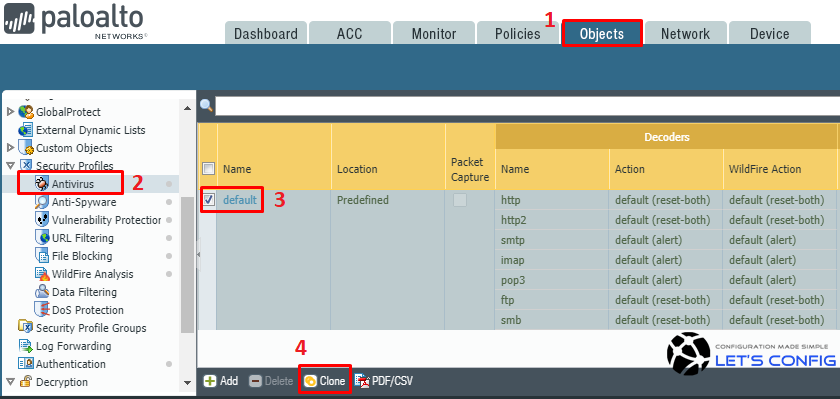
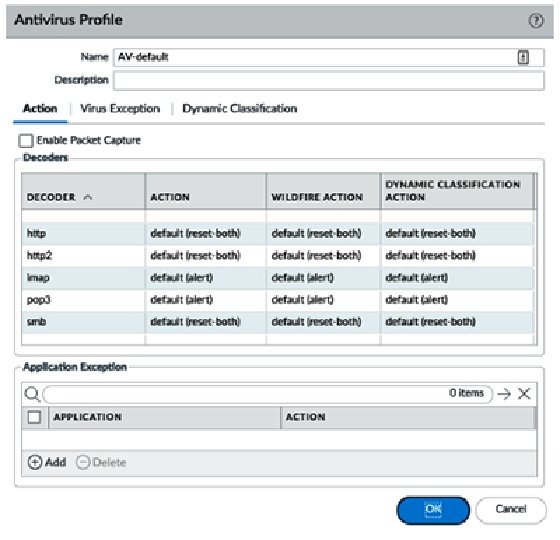
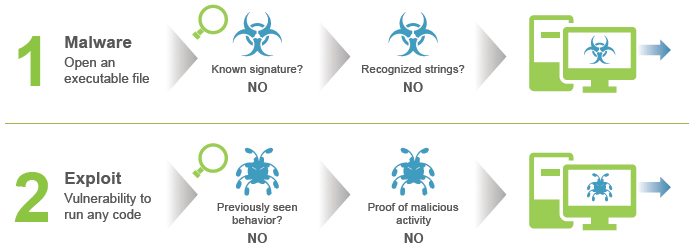
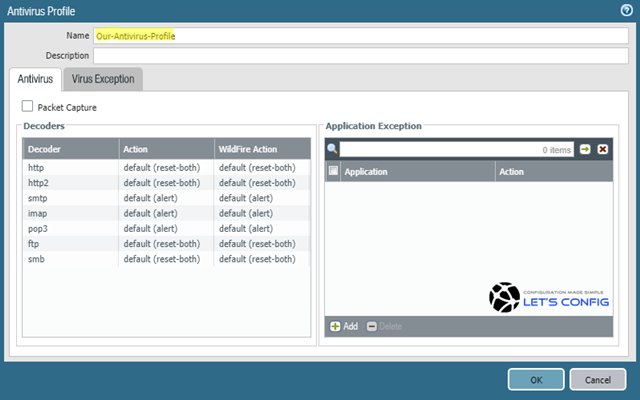
How to Use Anti-Spyware, Vulnerability and Antivirus Exceptions... - Knowledge Base - Palo Alto Networks
Vulnerability Exception Based Upon Source and Destination IP Ad... - Knowledge Base - Palo Alto Networks
Mitigate Vulnerabilities Through Proper Application of Threat P... - Knowledge Base - Palo Alto Networks